CloudGoat scenario 01 - sns_secrets (AWS, Pacu)
sns_secrets (Small / Easy)
In this scenario, you are given AWS credentials. Your task is to enumerate permissions and discover that you have the ability to list and subscribe to SNS topics. Use Pacu’s new modules, “sns__enum” and “sns__subscribe,” to subscribe to the topic. You will receive an email from the topic containing an API Key as a debug message. Next, use the AWS CLI to enumerate the API Gateways and find the path, method, stage, and resource of the API Gateway. Finally, perform a curl request with the API key to retrieve the final flag.
1 | ./cloudgoat.py create sns_secrets |
If you run above command, then you’ll get below information.
1 | [cloudgoat] terraform output completed with no error code. |
AWS SNS (Simple Notification Service)
A messaging service that allows creating topics and sending messages to subscribed recipients. In this challenge, you need to list SNS topics, subscribe to one, and receive an API key via email.
IAM (Identity and Access Management)
A service that manages user access permissions in AWS. It allows companies to assign detailed permissions to different teams and users based on their roles. For example, the development team can be granted access to EC2 and S3, while the database management team gets access to RDS. Like most access control systems, a root account manages everything, while other users receive individual accounts with limited permissions.
In this challange, you need to enumerate your permissions using the provided AWS credentials and check if you can list and subscribe to SNS topics.
Solve
1 | $ aws configure --profile sns-secrets |
If you enter the credentials obtained from the challenge, you can check your identity, similar to using the whoami command, with the following command.
1 | $ aws sts get-caller-identity --profile sns-secrets |
1. Enumeration IAM user’s permissions using the AWS CLI
We will use the unique ARN(Amazon Resouce Name) obtained from the challenge profile to enumerate policies.
1 | $ aws iam list-user-policies --user-name cg-sns-user-sns_secrets_cgidjt7xmtxtc7 --profile sns-secrets |
Now that we have retrieved the specific policy information, let’s examine its details.
1 | $ aws iam get-user-policy --user-name cg-sns-user-sns_secrets_cgidjt7xmtxtc7 --policy-name cg-sns-user-policy-sns_secrets_cgidjt7xmtxtc7 --profile sns-secrets |
To briefly explain how AWS SNS works, A publisher sends messages to an SNS topic such as server-alerts. These messages are delievered to subscribers through email or SMS.
(Publisher) –> (SNS Topic) –> (Subscriber)
Above IAM policy provided to the user allows the sns:Subscribe permission on all SNS topics. The key issue here is "Resource": "*". This permission grants the user the ability to subscribe to any topic. This is a critical vulnerability because it allows unauthorized users to subscribe to potentially sensitive topics.
Next, the policy also allows the "apigateway:GET". This permission grants to make GET requests to API Gateway resources. The user will need an API Key to authenticate and successfully interact with the API. Now, How can I get the API Key?
2. Subscribing to an SNS Topic using Pacu
We use Pacu which is an open-source AWS exploitation framework. With Pacu, we can enumerate SNS topics and subscribe to them. And also we can enumerate our IAM permissions using Pacu as shown below. First, create a new session and enter below command then it will import AWS Keys from the AWS CLI credentials file (~/.aws/credentials).
1 | Pacu (sns-secrets:No Keys Set) > import_keys sns-secrets |
There are two modules related to SNS. These modules are based on IAM profile, it means this profile(sns-secrets) can use only these modules when it comes to SNS.
1 | Pacu (sns-secrets:imported-sns-secrets) > search sns |
sns-secrets profile has the sns:ListTopics permission, so you can use the sns__enum module. Additionally, this profile has the sns:Subscribe permission, allowing you to use the sns__subscribe module.
You can use the help command to get more information about how to use each SNS-related module (sns__enum, sns__subscribe):
sns__enum: Lists and describes SNS topics. It’s used to enumerate the existing SNS topics in an AWS.sns__subscribe: Subscribes to a specific SNS topic. And also it allows to receive a subscription confirmation.
1 | Pacu (sns-secrets:imported-sns-secrets) > run sns__enum --region us-east-1 |
You can check the unique ARN(Amazon Resouce Name). In AWS, each resources(e.g EC2, S3, SNS Topic ..) have unique ARN.
1 | Pacu (sns-secrets:imported-sns-secrets) > run sns__subscribe --topics [TopicARN] --email [Email] |
After running this command, you can confirm the subscription via email. Once you confirm the SNS Topic subscription, you will receive an API Key for the API Gateway via email. As I mentioned before, this can be a vulnerability. You can send a GET request to the API Gateway using this API Key.
But why will you get the API Key? This is likely due to a developer’s mistake. Or the sns:Subscribe permission is too broadly configured, allowing users who shouldn’t have access to receive messages.
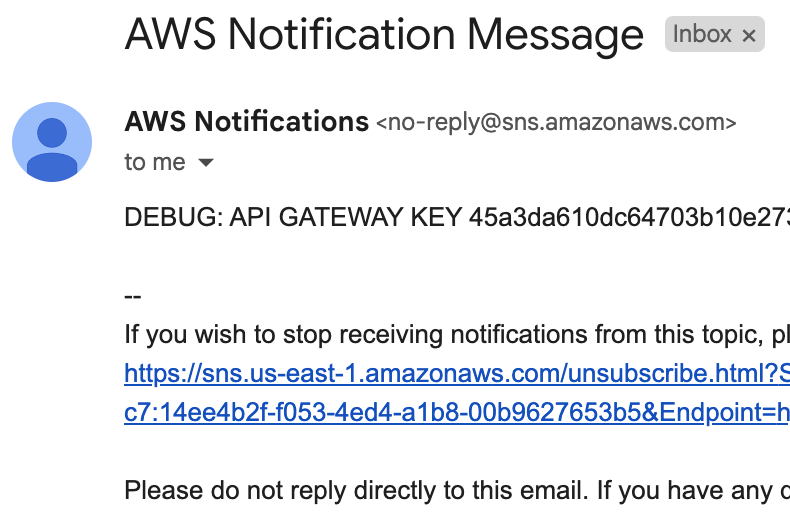
In this challenge, It says DEBUG in the email, so it is definitely not for a normal user.
3. Accessing the API Gateway and Get a Flag
After getting an API Key for the API Gateway, we can enumerate the available APIs, stages, and resources using AWS CLI. First, we list the API Gateway resources associated with the sns-secrets profile.
1 | $ aws apigateway get-rest-apis --profile sns-secrets --region us-east-1 |
The output shows an API named cg-api-sns_secrets_cgidjt7xmtxtc7 and ID is 43u8hxyd16. We will check available deployment stages using this ID.
1 | $ aws apigateway get-stages --rest-api-id 43u8hxyd16 --profile sns-secrets --region us-east-1 |
The prod-sns_secrets_cgidjt7xmtxtc7 stage is active. It means API requests can be sent to this endpoint.
1 | $ aws apigateway get-resources --rest-api-id 43u8hxyd16 --profile sns-secrets --region us-east-1 |
The /user-data resource supports GET requests. It means we can attempt to access and get user data through this path.
1 | https://[API-ID].execute-api.us-east-1.amazonaws.com/[stageName]/[resourcePath] |
Since we already got the API Key, we can now send a GET request to the API Gateway endpoint (/user-data) like this!
1 | $ curl -X GET \ |
Finally we got a flag and SuperAdmin account. This challenge shows how important it is to properly manage permissions and secure sensitive information in AWS.
1 | $ ./cloudgoat.py destroy sns_secrets |
And.. don’t forget destroy the deployed resources!!